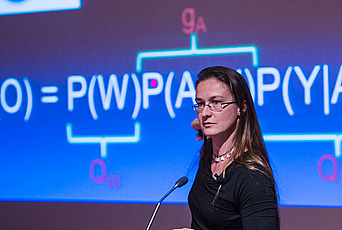How to Obfuscate
Some forms of obfuscation generate genuine but misleading signals—much as you would protect the contents of one vehicle by sending it out accompanied by several other identical vehicles, or defend a particular plane by filling the sky with other planes—whereas other forms shuffle genuine signals, mixing data in an effort to make the extraction of patterns more difficult.
TrackMeNot, developed in 2006 by Helen Nissenbaum, former Visitor in the School of Social Science, Daniel Howe, and Vincent Toubiana, exemplifies a software strategy for concealing activity with imitative signals. The purpose of TrackMeNot is to foil the profiling of users through their searches. It was designed in response to the U.S. Department of Justice’s request for Google’s search logs and in response to the surprising discovery by a reporter from The New York Times that some identities and profiles could be inferred even from anonymized search logs published by AOL Inc.
Read more at Nautilus.